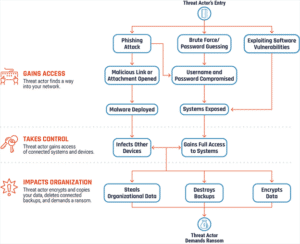
Ransomware is increasingly becoming a threat impacting organizations. The schematic illustration below is intended to depict how a ransomware incident can occur. Ransomware keeps managers and security professionals up at night because of the disruptive nature of cyberattacks.
What is Ransomware?
Ransomware is a type of malware that denies a user’s access to files or systems until a sum of money is paid.
The fear is certainly justified
The fear is certainly justified. The cost to remediate and recover from cyberattacks is consistently increasing yearly, and the number of attacks that organizations experience is also growing. Organizations are reporting a 7% increase in cyberattacks in terms of volume, and they are having a tough time keeping up with staff and budget limitations. Malefactors are taking advantage of increasingly lucrative and easier to deploy cyberattack campaigns and stratagems. In general, companies that are better prepared tend to cope better against such cyberattacks.
Ransomware as a service
Ransomware as a service has become its own industry. Several wrongdoers are purchasing ransomware campaigns that are created by highly skilled professionals. Ransomware as a service is the adversarial equivalent to as-a-service offerings provided by organizations to help reduce capital costs. Malefactors now have access to ransomware subscriptions executed by using operational expenditures significantly reducing the cost initiate attacks.
For example, the recently identified EvilProxy service had campaigns starting at just $150 USD[1]. In addition, campaigns like EvilProxy are emerging. EvilProxy was revolutionary in providing non-technical, non-sophisticated wrongdoers access to mature, professional-grade cyberattack resources through a simple point-and-click user interface similar to common e-commerce sites. As-a-service campaigns are illustrated by attackers repeatedly assaulting the same organization.
Organizations are being targeted multiple times post-ransom payment.
Smaller organizations are increasingly paying ransoms and being retargeted.
To make things worse, the average cost per data record compromised has increased from $40 to $42 USD[2]. The implications are that smaller organizations are often unable to recover when they are targeted by ransomware campaigns.
[1] https://resecurity.com/blog/article/evilproxy-phishing-as-a-service-with-mfa-bypass-emerged-in-dark-web
[2] IBM Cyber Threat Study.
Operational Challenges
Senior management deals with many challenges. Senior management is becoming an increasingly targeted group for spear phishing campaigns as they are often too busy to maintain strong cybersecurity hygiene. In addition, executives are having a difficult time managing resource constraints because skilled and experienced cybersecurity professionals are rare. There are currently more cybersecurity jobs requiring qualified personnel than there are individuals to fill the responsibilities[3]. This leads to higher costs for organizations looking to onboard security professionals.
[3] https://www.cyberseek.org/heatmap.html
The cost of technologies to mitigate ransomware are also increasing. As a result, organizations have fewer monetary resources to fund the necessary tools to prevent ransomware and recover from cyberattacks. Nearly one-quarter of organizations that have budgets do not have the capacity to sufficiently finance security operations[4]. These challenges are amplified by the stark realization that enterprise-grade technology solutions cost thousands to several hundred thousand dollars, while ransomware campaigns have starting costs at a fraction of the cost of mitigation.
[4] CDW Security Study 2022.
What Organizations Can Do to Prepare Themselves in the Event of a Ransomware
Organizations should strive to improve their recovery procedures after a cyberattack. This goes with having a risk-management focus when building their strategies.
Good Risk Management
Organizations should build and review their risk registers. Furthermore, they should be prioritizing and hierarchizing controls based on annual loss expectancy and putting that into their budget.
Annual loss expectancy = cost of risk being realized / how frequently it happens in one calendar year.
If companies expect ransomware to cost them $50,000 a year, then they should consider finding solutions that reduce risk, which should be less expensive than implementing cybersecurity controls. In the above example, a company must be willing to spend up to $40,000 per year to select people, processes, and technology in order to reduce the impact of ransomware threats to less than $10,000 per year.
Recovery and Continuity Planning
It is difficult to prevent motivated malefactors from compromising companies with ransomware, but companies have the power to improve their recovery, and continuity capabilities. Organizations should conduct business impact analyses frequently to determine which assets are critical and prioritize alternative processes. To add to this, organizations should test their plans to ensure that they can recover in a timely fashion. Tabletop exercises and simulations are effective ways to validate the effectiveness of incident response, recovery and business continuity to ensure that recovery objectives can be met. To augment the aforementioned tests, they should also strive to calculate Recovery Time Objectives (RTOs) to have a key metric for how long it takes to recover. For more information you can refer to our last July newsletter.
Security Awareness Training
Phishing remains one of the most common vectors for ransomware campaigns to propagate within companies. Businesses with security awareness programs experienced up to 85% decrease in suspicious links clicked on, thereby resulting in greater security[5]. Implementing security awareness training will help with detection and prevention of ransomware by proactively training users to spot abnormalities in email, SMS and social media messages
Strategic Partnerships
As previously pointed out, the cost of onboarding talent in-house is a challenge, and there is no guarantee that companies will be able to find worthwhile cybersecurity personnel. Companies should consider partnering with cybersecurity organizations that have subject matter experts in various security fields. These can be organizations responsible for detection and prevention such as Security Operations Centers (SOCs) or remediation resources such as dedicated incident response companies. Either way, split access to trained cybersecurity professionals can be an effective way to curtail some of the costly expenses associated with onboarding security personnel. Organizations should seek to network with subject matter experts in the cybersecurity industry to prepare for the increasingly complex risks associated with ransomware.
Conclusion
Ransomware is a threat to your organization. It is imperative that you prepare your processes, information system and your team for an attack.
Resources
Employee training
Awareness Training (ISC2)
Jigsaw | Phishing Quiz (Google)
Phishing Quiz (Cisco)
CyberSafe (Canadian Goververnment)
Cybersec101 (SereneRisc and the Canadian Government)
Executive Training
Simply Secure Training for SMB (Rogers Cybersecure Catalyst)
Guides
10 steps to an efective cybersecurity program (Rogers Cybersecure Catalyst)
How ransomware happens and how to stop it (Government of New-Zealand)
Ransomware Playbook (Canadian Centre for Cybersecurity)
How to Prevent and Recover From Ransomware (Canadian Centre for Cybersecurity)