How is the emergence of post-quantum cryptography (PQC) impacting the classical cybersecurity operations of SMEs? How are post-quantum algorithms being integrated into digital safety products so that SMEs may strengthen their traditional cybersecurity posture and future-proof their products?
The objective of our March 2025 Newsletter is to provide hands-on answers to these two basic questions. Post-quantum cryptography (PQC) has emerged in response to the potential vulnerabilities of current cryptographic systems posed by the advent of quantum computing technology. As quantum computers become more powerful and sophisticated, they could potentially break widely-used cryptographic algorithms – such as RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) – which are foundational to current data security. Post-quantum cryptography (PQC) aims to develop cryptographic algorithms that are resistant to quantum-generated attacks, thereby ensuring the uninterrupted protection of sensitive information. At the beginning of our March 2025 Newsletter, it is important to note that post-quantum cryptography (PQC) is distinct from quantum cryptography which leverages the principles of quantum mechanics to safeguard data.
Contextually speaking, it is also noteworthy for us to specify that for most SMEs, they will migrate to post-quantum algorithms automatically through upgrades to their current supplier systems. Nevertheless, underneath such a brief contextual explanation and before we attempt to answer our two basic questions, we have to acknowledge that this innovative subject matter is more complex, intricate and multi-faceted than it appears on the surface level. This is why we have to circumscribe succinctly post-quantum cryptography in light of 2 other cyber-safety tools: classical cryptography and quantum cryptography.
With reference to digital safety best practices, there are 3 fundamental cybersecurity concepts that we have to delineate clearly: classical cryptography, quantum cryptography, and post-quantum cryptography (PQC). The prefix “post” in post-quantum cryptography (PQC) designates post-quantum computing and not post-quantum cryptography (PQC). As such, quantum cryptography is very different from post-quantum cryptography (PQC). Intrinsically speaking, post-quantum cryptography (PQC) does not use quantum cryptography because it has to work on traditional computers.
Before we delve into the required answers to our two essential questions demarcated above, let us refresh our acquired knowledge regarding a brief contrast between classical cybersecurity and post-quantum cryptography (see Table 1); the conceptual definitions of the following three fundamental cybersecurity concepts: classical cryptography, quantum cryptography, and post-quantum cryptography (see Table 2); and a summarized comparative analysis between classical cryptography, quantum cryptography, and post-quantum cryptography (see Table 3). The monographs1,2,3,4,5 referenced in the footnotes below have been consulted, read through and synopsized for the meticulous writing of this multi-layered newsletter.
1 – Christof Paar, Jan Pelzl and Tim Güneysu. Understanding Cryptography: From Established Symmetric and Asymmetric Ciphers to Post-Quantum Algorithms. Hardcover 2nd Edition published on the 16th of May 2024 by Springer-Verlag GmbH, Heidelberger Platz 3, 14197 City of Berlin, Germany, 543 pages. Understanding Cryptography: From Established Symmetric and Asymmetric Ciphers to Post-Quantum Algorithms | SpringerLink
2 – Ravi Jay Gunnoo. Cybersecurity Education Compendium: Harnessing Digital Safety Best Practices Across the World. 1st Edition published in Paperback – Large Print Format and e-Book Version. Publication date: the 18th of September 2024. Publishing Company: Amazon Publishing USA, City of Seattle, State of Washington, USA, 728 pages. CYBERSECURITY EDUCATION COMPENDIUM: Harnessing Digital Safety Best Practices Across the World: Gunnoo, Ravi Jay: 9798336620344: Books – Amazon.ca
3 – Douglas Robert Stinson and Maura B. Paterson. Cryptography: Theory and Practice – Textbooks in Mathematics. Paperback 4th Edition published on the 21st of January 2023 by Routledge/CRC Press – An Imprint of the Taylor & Francis Book LLC, 6000 Broken Sound Parkway NW, Boca Raton, Florida 33487-2742, United States of America, 598 pages. Cryptography: Theory and Practice – 4th Edition – Douglas Robert Stinson and Maura B. Paterson
4 – Roger A. Grimes. Cryptography Apocalypse: Preparing for the Day When Quantum Computing Breaks Today’s Crypto. Paperback 1st Edition published on the 12th of November 2020 by John Wiley & Sons, Inc., 111 River Street, Hoboken, New Jersey 07030, United States of America, 272 pages. Cryptography Apocalypse: Preparing for the Day When Quantum Computing Breaks Today’s Crypto | Wiley
5 – Ethan Westwood. Post-Quantum Cryptography: Beyond Quantum Threats: Unlocking the Unparalleled Security with CPQ. Paperback Edition published on the 17th of December 2024 by Amazon USA Publishing, City of Seattle, State of Washington, United States of America, 203 pages. Post-Quantum Cryptography: Securing the Future of Digital Communications: Westwood, Ethan, Books, SMART: 9798304019866: Books – Amazon.ca
TABLE 1 – Brief Contrast Between Classical Cybersecurity and Post-Quantum Cryptography
To reactivate our acquired knowledge, what is basically classical cybersecurity? In a nutshell, on the one hand, classical cybersecurity (synonyms: computer security, electronic systems protection, digital security, electronic data defense, IT security, etc.) is the protection of computer software, systems and networks from cyber threats that can lead to unauthorized information disclosure, theft or damage to hardware, software or data, as well as from the disruption or misdirection of the services they provide. On the other hand, post-quantum cryptography (PQC) magnifies, increases and improves classical cybersecurity at a higher level. How is it able to do so? Below are some synthesized explanations in tabular format.
| Brief Contrast Between Classical Cybersecurity &
Post-Quantum Cryptography |
||
| Features | Classical Cybersecurity | Post-Quantum Cryptography (PQC) |
| Scope | Broad, including protection against malware, phishing, APTs, and other threats. | Focused specifically on addressing cyber threats from quantum computing. |
| Methods | Firewalls, intrusion detection, classical encryption (e.g.: RSA, ECC, AES), and multi-factor authentication (MFA). | Quantum-resistant algorithms (e.g.: lattice-based, hash-based, code-based cryptography). |
| Challenges | Adapting to evolving threats, mitigating zero-day vulnerabilities, and balancing usability with security. | Integrating new algorithms with current IT systems and standardization of solutions. |
| Focus | Real-time cyber threat detection, alleviation, and IT systems resilience. | Future-proofing encryption against quantum-enabled attacks. |
| Purposes | Safeguarding IT systems, data, and networks from a sprawling range of cyber threats. | Preventing the infringement of encrypted data by quantum computers. |
| Current Encryption | Relies on classical cryptography methods like RSA and ECC. | Creates algorithms resistant to quantum decryption capabilities. |
Nota Bene (N.B.)
- Classical cybersecurity and post-quantum cryptography are interconnected fields but they address different IT systems challenges and cyber threats. Whereas classical cybersecurity is a broader and all-encompassing discipline, post-quantum cryptography (PQC) is a specialized area within classical cybersecurity, focusing mainly on the adaptation to the emerging quantum computing era and bringing traditional cybersecurity to a higher level. The transition to post-quantum cryptography (PQC) is crucial as quantum computers become more advanced, potentially rendering some traditional encryption obsolete.
- Whereas classical cybersecurity covers a far-reaching assortment of cyber threats, post-quantum cryptography (PQC) is crucial for safeguarding public key encryption – the backbone of secure online data, information, communications and transactions – against emerging quantum computing risks. In a nutshell, post-quantum cryptography (PQC) is in essence a specialized subset of classical cybersecurity, tailored to counter the unique challenges posed by quantum computing technology. Other essential subsets of classical cybersecurity, as an all-inclusive field of expertise, are illustrated in the Venn Diagram designed on the subsequent page.
FIGURE 1 – Venn Diagram Illustrating Subsets of Classical Cybersecurity as an All-Encompassing Discipline of Computer Science Knowledge

The above Venn Diagram is an illustrative synopsis of the substantive contents expounded in Table 1, Table 2 and Table 3 of this March 2025 Newsletter. Emanating from that synopsized Venn Diagram, we can extrapolate that classical cryptography, post-quantum cryptography (PQC), and quantum cryptography represent essential subsets of cybersecurity, each addressing different challenges in safeguarding online data, information, communications and transactions. Altogether, the above subsets form a multi-faceted approach to maintaining cybersecurity in the face of evolving threats. While classical cryptography underpins today’s Information Technology (IT) systems, post-quantum cryptography (PQC) prepares us for quantum-era challenges generated by quantum computing technology, and quantum cryptography explores the boundaries of secure online data, information, communications and transactions.
TABLE 2 – For Our Knowledge Retention: Abridged Conceptual Definitions of Classical Cryptography, Post-Quantum Cryptography (PQC) & Quantum Cryptography
| Classical Cryptography, Post-Quantum Cryptography (PQC) & Quantum Cryptography:
Abridged Conceptual Definitions |
||
| Classical Cryptography | Post-Quantum Cryptography (PQC) | Quantum Cryptography |
| Classical cryptography is the practice and study of securing online data, information, communications and transactions through the use of codes, so that only those for whom the online data, information, communications and transactions are intended can exclusively read and process them.
Classical cryptography involves techniques like encryption (converting plaintext into unreadable ciphertext) and decryption (turning ciphertext back into plaintext). Classical cryptography ensures confidentiality, integrity, authentication, and non-repudiation in digital data, information, communications and transactions. |
Post-quantum cryptography (PQC) refers to cryptographic algorithms designed to withstand the power of quantum computers.
Unlike classical cryptography, which is vulnerable to attacks from advanced quantum machines, such cryptographic algorithms rely on tested mathematical problems that are believed to be resistant to quantum computing techniques. The goal of post-quantum cryptography (PQC) is to ensure the long-term security of digital systems, even in a future where quantum computers become capable of breaking current encryption methods like RSA and ECC. These post-quantum cryptographic algorithms are being developed to seamlessly integrate with existing digital infrastructure while providing enhanced protection. |
Quantum cryptography is a cutting-edge field that uses the principles of quantum mechanics to secure communication.
Its primary focus is on quantum key distribution (QKD), which allows two parties to share encryption keys securely, detecting any eavesdropping attempts in real time. By leveraging quantum phenomena like superposition and entanglement, it provides unparalleled security, as any unauthorized interception of data will disturb the system, alerting the legitimate users. |
| Classical cryptography is the science and art of protecting information by converting it into a secure format.
Classical cryptography uses mathematical algorithms and techniques, such as encryption (converting readable data into unreadable code) and decryption (turning the code back into its original form), to safeguard communication and data from unauthorized access or tampering. Classical cryptography plays a critical role in ensuring data privacy, data integrity, and secure multi-factor authentication (MFA) in fields like online banking services, messaging apps, and digital signatures. |
Post-quantum cryptography (PQC) is a field of cryptography that focuses on developing cryptographic algorithms capable of withstanding attacks from powerful quantum computers.
As quantum computers have the potential to break traditional encryption methods like RSA and ECC by solving their mathematical problems much faster, post-quantum cryptography (PQC) aims to ensure IT systems security even in a quantum-powered future. These new algorithms rely on mathematical problems that are believed to remain difficult for quantum computers to solve, such as lattice-based cryptography (LBC), hash-based cryptography (HBC), and multivariate polynomial-based approaches. The goal is to provide long-term protection for data and communications without requiring entirely new infrastructure, making it a critical area of research for maintaining digital security. |
Quantum cryptography is an advanced method of securing communication by utilizing the principles of quantum mechanics. Its core concept is Quantum Key Distribution (QKD), which allows two parties to exchange encryption keys in a way that is theoretically immune to eavesdropping.
The security of quantum cryptography lies in unique quantum phenomena such as:
Unlike classical cryptography, which relies on complex mathematical algorithms, quantum cryptography leverages the fundamental laws of physics for unmatched security. This could hold great promise in safeguarding data, particularly in a future where quantum computers could break conventional encryption methods. |
Potential Impact of Quantum Computing Technology on Encryption=Information Storage for Future Decryption
Figure 2: Interception of Encrypted Information and Storing It for Future Decryption
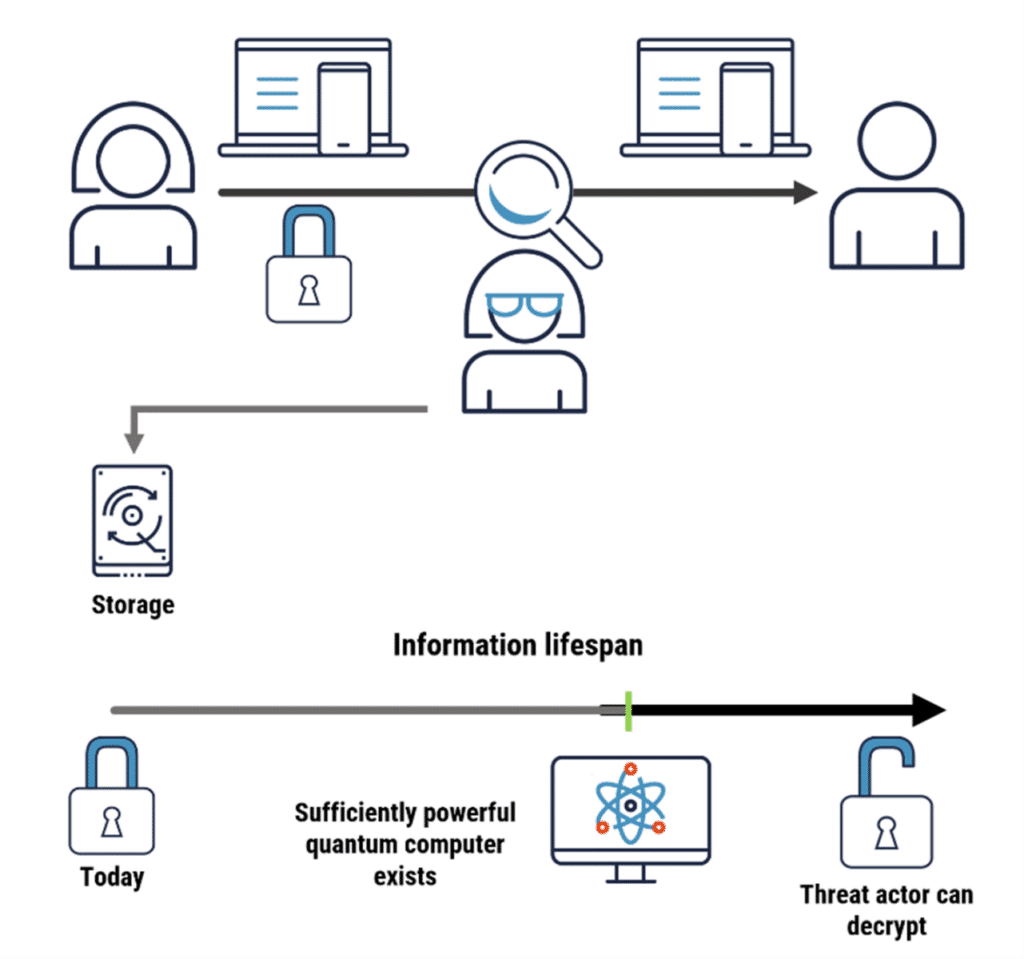
Source: Canadian Centre for Cybersecurity – Cyber Security Guidance, Preparing your Organization for the Quantum Threat to Cryptography (ITSAP.00.017)
Potential Impact of Quantum Computing Technology on Authentication=Impersonation of Trusted IT Systems
Figure 3: Use of Powerful Quantum Computers for Impersonation

Source: Canadian Centre for Cybersecurity – Cyber Security Guidance, Preparing your Organization for the Quantum Threat to Cryptography (ITSAP.00.017)
Post-Quantum Cryptography (PQC) Transition
Figure 4: Post-Quantum Cryptography (PQC) Progression

Source: Canadian Centre for Cybersecurity – Cyber Security Guidance, Preparing your Organization for the Quantum Threat to Cryptography (ITSAP.00.017)
TABLE 3 – Summarized Comparative Analysis Between Classical Cryptography, Quantum Cryptography, & Post-Quantum Cryptography (PQC)
| Characteristics | Classical Cryptography | Quantum Cryptography | Post-Quantum Cryptography (PQC) |
| Definitions | The practice of securing data using mathematical algorithms and keys. | Uses principles of quantum mechanics to secure communication, primarily through quantum key distribution (QED). | Focuses on developing algorithms resistant to attacks from quantum-powered computers. |
| Security Foundations | Relies on computational problems that are hard to solve with classical computers. | Leverages quantum phenomena like superposition and entanglement for unmatched security. | Built on mathematical problems that are believed to be hard for both classical and quantum-powered computers to solve. |
| Purposes | Ensures confidentiality, integrity, and authentication in online communications and data storage. | Protects public key encryptions and ensures eavesdropping can be detected in real time. | Safeguards systems and data from quantum computing threats while being compatible with current infrastructure. |
| Vulnerabilities | Potentially breakable by quantum computers with Shor’s algorithm. | Theoretically unbreakable if implemented perfectly, but relies on quantum infrastructure. | Designed to withstand quantum attacks while compatible with existing classical systems. |
| Applications | Online banking services, secure text messaging, digital signatures, etc. | Limited to specialized applications like secure key distribution in experimental setups. | Designed to replace current cryptographic systems to ensure future-proof security. |
| Statuses of Development | Well-established and widely used in modern digital systems. | Emerging technology, mainly used in experimental and niche applications. | Actively researched and under development to prepare for the impacts of post-quantum computing. |
N.B. for Table 3 – Summarized Comparative Analysis: It should be noted that classical cryptography, quantum cryptography & post-quantum cryptography (PQC) deal with different cybersecurity needs & challenges, with quantum cryptography offering theoretical advancements & post-quantum cryptography (PQC) providing solutions for the future of encryption & decryption. Each digital safety practice plays a crucial role in the evolving landscape of cybersecurity. On the one hand, quantum cryptography is innovative but it is still limited by its dependence on specialized hardware. On the other hand, post-quantum cryptography (PQC) is designed to be a practical bridge to a secure future, even in the face of advancing quantum computers.
Pre-Emptive Question 1: What are specific encryption methods at risk from quantum computing technology?
Specific Encryption Methods at Risk from Quantum Computing Technology
Quantum computing technology poses a significant threat to several widely used encryption methods, particularly those based on public-key cryptography. Shortened hereunder are the key methods at risk:
- RSA (Rivest-Shamir-Adleman): This algorithm relies on the difficulty of factoring large numbers, a problem that quantum computers can solve efficiently using Shor’s algorithm.
- ECC (Elliptic Curve Cryptography): ECC is based on the difficulty of solving elliptic curve discrete logarithm problems, which quantum computers can also tackle effectively.
- DSA (Digital Signature Algorithm): Similar to RSA and ECC, DSA is vulnerable to quantum computing technology attacks due to its reliance on discrete logarithm problems.
Symmetric encryption methods like AES (Advanced Encryption Standard) are less vulnerable, but larger key sizes (for instance: AES-256) are recommended to enhance resistance against quantum computing technology cyber-attacks.
Pre-Emptive Question 2: What are some significant consequences faced by SMEs failing to migrate to post-quantum cryptography (PQC)?
SMES that fail to transition to post-quantum cryptography (PQC) face significant risks as quantum computing technology advances. Hereafter are some potential consequences:
- Sensitive Data Breaches: Quantum computers could break widely used encryption algorithms like RSA and ECC, exposing sensitive data to theft or misuse.
- Harvest Now, Decrypt Later Attacks: Adversaries might store encrypted data now and decrypt it later when quantum computers become powerful enough.
- Operational Disruption: Critical systems relying on outdated encryption could be compromised, leading to disruptions in operations.
- Loss of Trust: Customers and partners may lose confidence in an organization’s ability to protect data, damaging its reputation.
- Regulatory Non-Compliance: Governments and industries may mandate quantum-resistant encryption, and non-compliance could result in penalties.
- Economic Impact: Recovering from breaches or upgrading systems reactively could be far more costly than Pre-Emptive adoption of post-quantum cryptography (PQC).
Although it appears to entail demanding procedures, transitioning to post-quantum cryptography (PQC) is a multi-faceted but indispensable step to future-proof security for the eventual benefits of SMEs.
Pre-Emptive Question 3: What are common challenges encountered by SMEs during the post-quantum cryptography (PQC) transition?
Common Challenges Faced by SMEs During the Transition to Post-Quantum Cryptography (PQC)
Transitioning to post-quantum cryptography (PQC) is a significant challenge for small and medium-sized enterprises (SMEs) that integrate encryptions within their products. Briefly expounded below are some common hurdles they are encountering:
- Performance and Efficiency: post-quantum cryptography (PQC) algorithms often require more computational power, memory, and energy, which can strain the limited resources of SMEs.
- Cost and Resource Allocation: Implementing post-quantum cryptography (PQC) involves significant financial investment in upgrading systems, training staff, and ensuring compliance with new standards.
- Algorithm Maturity: Many post-quantum cryptography (PQC) algorithms are still in the experimental phase and they lack the extensive testing and validation of traditional cryptographic procedures.
- Nevertheless, some post-quantum cryptography (PQC) algorithms are currently being evaluated by the U.S. NIST, and some other post-quantum cryptography (PQC) algorithms have been selected and approved by the U.S. NIST. In August 2024, the U.S. NIST published one algorithm standard for key establishment: ML-KEM (CRYSTALS-Kyber) and two additional algorithm standards for digital signatures: ML-DSA (CRYSTALS-Dilithium) and SLH-DSA (SPHINCS+).
- Security Risks: New post-quantum cryptography (PQC) schemes may introduce vulnerabilities, such as susceptibility to side-channel attacks, requiring specialized expertise to mitigate.
- Integration Challenges: Combining post-quantum cryptography (PQC) with existing cryptographic systems can be complex, especially for SMEs with limited technical expertise.
- Regulatory and Compliance Issues: Keeping up with evolving standards and ensuring compliance can be overwhelming for smaller organizations like SMEs.
- Lack of Awareness and Readiness: Many SMEs delay action due to misconceptions about the urgency of transitioning to post-quantum cryptography (PQC).
Pre-Emptive Question 4: What feasible and workable strategies are available for SMEs to overcome challenges during the transition or migration to post-quantum cryptography (PQC)?
Feasible and Workable Strategies Available for SMEs to Overcome Challenges During the Transition to Post-Quantum Cryptography (PQC)
Abbreviated as follows are some feasible and workable strategies that SMEs can adopt to effectively transition to post-quantum cryptography (PQC) while overcoming common challenges:
1. Raise Awareness and Educate Stakeholders
- Conduct workshops or training for employees to understand the urgency and importance of post-quantum cryptography (PQC).
- Keep leadership informed about the potential risks of quantum computing technology to existing cryptographic systems.
2. Conduct a Cryptographic Inventory: Conduct a thorough inventory of all cryptographic systems, protocols, and data assets to identify vulnerabilities to quantum computing technology attacks.
3. Start with Risk Assessments
- Identify sensitive data and systems that are most vulnerable to quantum attacks.
- Prioritize securing critical assets first to allocate resources effectively.
4. Adopt Post-Quantum Cryptography (PQC): Transition to quantum-resistant cryptographic algorithms that are designed to withstand quantum computing technology attacks. Engage with standardization bodies like the Canadian Centre for Cyber Security1, the U.S. NIST2 and CyberSecure Canada3 to adopt approved post-quantum cryptography (PQC) standards.
5. Leverage Expert Guidance and Knowledge Sharing
- Collaborate with cybersecurity firms or consultants that specialize in post-quantum cryptography (PQC).
- Use industry resources like government guidelines (CyberSecure Canada, Canadian Centre for Cyber Security) and the U.S. NIST post-quantum cryptography (PQC) standardization project.
- Collaborate with industry peers, academia, and cybersecurity agencies to stay updated on advancements in quantum-safe technologies.
6. Establish Governance Frameworks: Establish governance frameworks to oversee the transition to quantum-safe cryptography. Develop a long-term strategy to maintain cryptographic resilience.
7. Adopt a Hybrid Approach
- Gradually implement post-quantum cryptography (PQC) by integrating it with existing cryptographic methods, allowing smoother transitions and minimizing disruptions.
8. Leverage Cloud Computing Technology Services
- Partner with cloud computing technology service providers who offer quantum-safe solutions, reducing the need for SMEs to implement everything in-house.
9. Optimize Budget and Resources
- Apply for government grants or incentives aimed at improving cybersecurity for SMEs.
- Pool resources or form consortiums with other SMEs to share costs and knowledge.
10. Focus on Scalable Solutions
- Select post-quantum cryptography (PQC) algorithms that are adaptable to future changes and compatible with evolving technologies.
11. Test, Validate and Implement
- Run simulations and pilot programs to test the performance and security of post-quantum cryptography (PQC) algorithms before full deployment.
- Test quantum-safe algorithms in controlled environments before full-scale implementation. Ensure compatibility with existing systems.
- Monitor for updates as algorithms are refined and finalized.
12. Stay Updated on Post-Quantum Cryptography (PQC) Standards
- Continuously monitor developments in post-quantum cryptography (PQC) standards to guarantee compliance with global and regional regulations.
- Regularly update cryptographic systems and monitor advancements in quantum computing technology to stay ahead of emerging cyber threats.
1 – Government of Canada – Canadian Centre for Cyber Security. Cyber Security Guidance Awareness Series. Preparing your organization for the quantum threat to cryptography (ITSAP.00.017). February 2025. Preparing your organization for the quantum threat to cryptography (ITSAP.00.017) – Canadian Centre for Cyber Security
2 – Government of the United States of America – National Institute of Standards and Technology – NIST: Computer Security Resource Center (CSRC) – Information Technology Laboratory. Status Report on the 4th Round of the NIST Post-Quantum Cryptography Standardization. Post-Quantum Cryptography | CSRC
3 – Government of Canada – CyberSecure Canada – Innovation, Science and Economic Development Canada. Certification Information and Certification Mark Display Requirements. CyberSecure Canada
Pre-Emptive Question 5: Could you please provide some key characteristics of post-quantum cryptography (PQC) that are relevant for SMEs
Some Key Features of Post-Quantum Cryptography (PQC) for SMEs
Post-quantum cryptography (PQC) offers several key features that are particularly relevant for small and medium-sized enterprises (SMEs):
- Quantum-Resistant Algorithms: Post-quantum cryptography (PQC) uses algorithms designed to withstand attacks from both classical and quantum computers, ensuring long-term data security.
- Interoperability: Many post-quantum cryptography (PQC) solutions are being developed to work alongside existing cryptographic systems, allowing SMEs to migrate progressively without disrupting their daily business operations.
- Future-Proofing: By adopting post-quantum cryptography (PQC), SMEs can protect sensitive data from “harvest-now, decrypt-later” attacks, where encrypted data is stolen now and decrypted later when quantum computers become more advanced.
- Compliance with Emerging Standards: post-quantum cryptography (PQC) is in harmony with evolving regulatory requirements and industry standards, helping SMEs stay compliant as quantum computing technology becomes more prevalent.
- Scalability: post-quantum cryptography (PQC) solutions are being designed to cater to businesses of all sizes, making them particularly accessible and scalable for SMEs.
The above key characteristics make post-quantum cryptography (PQC) a decisive consideration for SMEs aiming to safeguard their daily business operations against future quantum computing technology threats.
Pre-Emptive Question 6: For our clear understanding, could you please offer some examples of quantum-resistant algorithms that could be helpful to SMEs?
Pre-Emptive Question 6: For our clear understanding, could you please offer some examples of quantum-resistant algorithms that could be helpful to SMEs?
Some Examples of Quantum-Resistant Algorithms that Could Be of Assistance to SMEs
Abridged hereafter are some notable examples of quantum-resistant algorithms that could be of assistance to small and medium-sized enterprises (SMEs):
- Lattice-Based Cryptography (LBC): This relies on the complexity of lattice problems, such as the Learning with Errors (LWE) problem. Algorithms like Kyber and Dilithium fall under this category.
- Hash-Based Cryptography (HBC): These algorithms use cryptographic hash functions to create secure digital signatures. The Merkle Signature Scheme is a well-known example.
- Code-Based Cryptography (CBC): Based on the difficulty of decoding random linear codes. The McEliece cryptosystem is a prominent example.
- Multivariate Quadratic Equations (MQE): These algorithms rely on the difficulty of solving systems of multivariate quadratic equations over finite fields.
The above quantum-resistant algorithms are being currently evaluated and standardized by organizations like the U.S. National Institute of Standards and Technology – NIST1 to ensure they are robust against quantum computing attacks. However, some other post-quantum cryptography (PQC) algorithms have been selected and approved by the U.S. NIST. In August 2024, the U.S. NIST published one algorithm standard for key establishment: ML-KEM (CRYSTALS-Kyber) and two additional algorithm standards for digital signatures: ML-DSA (CRYSTALS-Dilithium) and SLH-DSA (SPHINCS+).
1 – Government of the United States of America – National Institute of Standards and Technology – NIST: Computer Security Resource Center (CSRC) – Information Technology Laboratory. Status Report on the 4th Round of the NIST Post-Quantum Cryptography Standardization. Post-Quantum Cryptography | CSRC
Pre-Emptive Question 7: For the benefits of SMES, could you succinctly explain why is lattice-based cryptography (LBC) considered as a fascinating and robust area of post-quantum cryptography (PQC)?
Lattice-Based Cryptography: A Fascinating & Robust Area of Post-Quantum Cryptography (PQC)
Lattice-based cryptography1,2 is a fascinating and robust area of post-quantum cryptography (PQC) that relies on the mathematical properties of lattices. Concisely written below for the benefits of SMEs is a synopsis of lattice-base cryptography.
The Mathematical Concept of Lattice in a Nutshell
A lattice is a grid-like structure in multidimensional space, formed by integer combinations of a set of basis vectors. Imagine a 2D grid of points created by two vectors. Now extend this concept to higher dimensions. Lattices are intrinsically infinite and they have unique mathematical properties that make certain problems computationally hard to solve.
Core Concepts in Lattice-Based Cryptography (LBC)
- Hard Problems: The security of lattice-based cryptography (LBC) is based on the difficulty of solving certain lattice problems, such as:
- Shortest Vector Problem (SVP): Finding the shortest non-zero vector in a lattice.
- Learning With Errors (LWE): A problem involving noisy linear equations, which is computationally hard to solve.
- Quantum Resistance: Unlike traditional cryptographic methods like RSA or ECC, lattice-based cryptography (LBC) schemes are resistant to attacks from quantum computers, making them ideal for post-quantum cryptography (PQC).
- Concrete Applications:
- Encryption: Algorithms like CRYSTALS-Kyber use lattice-based principles for protected key exchange.
- Digital Signatures: CRYSTALS-Dilithium is a lattice-based algorithm for creating safeguarded digital signatures.
- Fully Homomorphic Encryption (FHE): Lattice-based cryptography (LBC) enables FHE, allowing computations on encrypted data without decryption.
- Efficiency and Scalability: Lattice-based schemes are computationally efficient and scalable, making them suitable for a wide range of applications, from small devices to large-scale systems.
Promising Importance of Lattice-Based Cryptography (LBC)
Lattice-based cryptography (LBC) is one of the most promising approaches to securing data in a future where quantum computers could break traditional encryption. Its mathematical foundation ensures long-term security and adaptability. The promising importance of lattice-based cryptography (LBC) lies in its ability to provide strong, future-proof security in an increasingly digital and quantum-driven world. Summarized below is why lattice-based cryptography (LBC) is so crucial for the implementation of best cybersecurity practices:
- Post-Quantum Security: Traditional cryptographic systems, such as RSA and ECC, are vulnerable to quantum computers. Lattice-based cryptography (LBC) is quantum-resistant, ensuring that sensitive data remains secure even as quantum computing becomes more advanced.
- Enhanced Privacy: It enables advanced technologies like Fully Homomorphic Encryption (FHE), which allows data to be processed while still encrypted. This is critical for maintaining privacy in sensitive fields like health care, governmental and military secrets, financial management, medical records, and cloud computing services.
- Versatility: Beyond standard encryption and authentication, lattice-based cryptography (LBC) supports innovative applications like secure multiparty computation and zero-knowledge proofs, paving the way for more secure and private interactions in digital spaces.
- Wide Applicability: Lattice-based cryptography (LBC) inherent flexibility means it can be tailored to a variety of platforms, from high-performance servers to resource-constrained devices like IoT gadgets, making it suitable for diverse real-world scenarios.
- National Security: Governments and organizations are adopting lattice-based systems to safeguard critical infrastructure and communications from future cyber threats.
By addressing the limitations of traditional cryptography and preparing for emerging challenges, lattice-based cryptography (LBC) is becoming an essential pillar of secure digital infrastructure.
Some Real-World Applications of Lattice-Based Cryptography (LBC)
Lattice-based cryptography (LBC) is a captivating field of cybersecurity with significant real-world applications, especially as we prepare for the post-quantum cryptography (PQC) era. Concisely described hereunder are some prominent cases in point:
- Post-Quantum Security: Lattice-based cryptography is resistant to quantum computing attacks, making it a cornerstone of post-quantum cryptographic (PQC) standards. It ensures secure communication even against the computational power of quantum computers.
- Digital Signatures: It enables the creation of secure digital signatures, which are essential for verifying the authenticity of digital documents and transactions.
- Homomorphic Encryption: This allows computations to be performed on encrypted data without decrypting it first. It is particularly useful in privacy-preserving data analysis and cloud computing.
- Secure Multiparty Computation: Lattice-based cryptography (LBC) facilitates collaborative computations where respective parties can jointly compute a function over their inputs while keeping those inputs private.
- Data Protection in Government and Military: Its robustness makes it ideal for securing sensitive information in sensitive government and military communications.
- Commercial Applications: organizations and SMEs can use lattice-based cryptography (LBC) to protect customer data, secure online transactions, and ensure the integrity of their digital systems.
- Research and Development: Many organizations and academic institutions are actively working on research and development to improve the efficiency and scalability of lattice-based cryptography (LBC) schemes for broader adoption.
The versatility and quantum resistance of lattice-based cryptography (LBC) make it a promising candidate for the future of protected online communications and transactions. The above real-world applications demonstrate the versatility and importance of lattice-based cryptography (LBC) in building a safe and sound digital future.
1 – Sujoy Sinha Roy and Ingrid Verbauwhede. Lattice-Based Public-Key Cryptography in Hardware: Computer Architecture and Design Methodologies. Paperback 1st Edition published on the 25th of November 2020 by Springer-Verlag GmbH, Heidelberger Platz 3, 14197 City of Berlin, Germany, 201 pages. Lattice-Based Public-Key Cryptography in Hardware | SpringerLink
2 – Jeffrey Hoffstein, Jill Pipher and Joseph H. Silverman. An Introduction to Mathematical Cryptography: Undergraduate Texts in Mathematics. Hardcover 2nd Edition published on the 11th of September 2014 by Springer Science + Business Media Publishing, 1 New York Plaza, New York City, United States of America, 538 pages. An Introduction to Mathematical Cryptography | SpringerLink
Pre-Emptive Question 8: What are the practical steps to prepare SMEs for managing successfully quantum threats related to post-quantum cryptography (PQC)?
Practical Steps to Prepare SMEs for Managing Successfully Quantum Threats Related to Post-Quantum Cryptography (PQC)
SMEs are recommended to take the following practical steps to help them manage successfully quantum threats related to post-quantum cryptography (PQC):
- Identify systems (internal and client-facing), applications, gateways and supporting security components that will need to be cryptographically transitioned.
- Supporting security components can include:
- Public key infrastructure (PKI)
- Web servers
- Authorization frameworks
- Authentication directories
- Protected domain name system (DNS)
- Pay close attention to custom systems and to software developed in-house or provided by smaller vendors.
- Ask vendors about their plans to include standardized validated PQC (e.g.: Cryptographic Module Validation Program – CMVP) in future updates to IT systems.
- This effort is generally called developing a cryptographic inventory.
- Supporting security components can include:
- Identify legacy systems that cannot be transitioned or replaced, and develop a risk-managed approach to protect them. An example of a solution would be tunnelling traffic through a post-quantum cryptography (PQC) that is protected by a virtual private network.
- Evaluate the sensitivity and lifespan of your organization’s information to identify information that may be at risk (as part of ongoing risk assessment processes). This will help you prioritize the transition work to post-quantum cryptography (PQC).
- Review your IT lifecycle management and develop plans to transition to post-quantum cryptography (PQC), when available.
- Budget for potentially significant software and hardware updates (including IT support staff) as the timeframe for necessary replacement approaches.
- Educate yourself & your teams on the emerging quantum threats and future quantum technologies.
- Ask your vendors about their plans to implement post-quantum cryptography (PQC) or to include post-quantum cryptography (PQC) in future updates to determine if your organization will need to acquire new hardware or software.
- Ensure that your vendor is using standardized, validated cryptography, such as possessing Federal Information Processing Standards (FIPS) accreditation.
- Leverage a cryptographic inventory to become cryptographically agile and allow for easier changes to cryptography in deployed systems. For more information refer to Guidance on becoming cryptographically agile (ITSAP.40.018).
- Update and patch systems as frequently as possible.
Conclusion
Upcoming Main Challenges & Future Prospects of Post-Quantum Cryptography (PQC)
To wrap up our March 2025 Newsletter, we have to positively point out that the future prospects of post-quantum cryptography (PQC) are shaping up to be altogether promising, challenging and transformative as the world prepares for the post-quantum cryptography (PQC) era. Below is an overview of the main challenges and future prospects1 regarding this innovative field of best cybersecurity practices:
Upcoming Main Challenges of Post-Quantum Cryptography (PQC)
- Algorithm Maturity:
- Many post-quantum cryptography (PQC) algorithms are still in the experimental phase and require extensive testing to ensure their reliability and security.
- Performance and Efficiency:
- Post-quantum cryptography (PQC) algorithms often demand more computational resources, which can impact IT systems performance, especially for resource-constrained devices.
- Integration Complexity:
- Transitioning to post-quantum cryptography (PQC) involves integrating new algorithms with existing IT systems, which can be technically challenging and time-consuming.
- Side-Channel Vulnerabilities:
- New cryptographic schemes may introduce vulnerabilities, such as susceptibility to side-channel attacks, requiring robust mitigation strategies.
- Cost and Resource Allocation:
- Implementing post-quantum cryptography (PQC) can be expensive, particularly for small and medium-sized enterprises (SMEs) with limited budgets.
- Global Standardization:
- Achieving consensus on post-quantum cryptography (PQC) standards across industries and regions is a complex, multifarious and ongoing process.
Future Prospects of Post-Quantum Cryptography (PQC)
- Enhanced Security:
- Post-quantum cryptography (PQC) will provide robust protection against quantum computing threats, safeguarding sensitive data and communications.
- Standardization Efforts:
- Organizations like the U.S. NIST are working with academia and industries on Research and Development (R&D) to pursue the development and implementation of quantum-safe solutions in order to finalize post-quantum cryptography (PQC) standards, thereby paving the way for widespread adoption.
- Integration with Emerging Technologies:
- Post-quantum cryptography (PQC) will be incorporated into blockchain, Internet of Things (IoT), and cloud computing services, ensuring these technologies remain secure in the quantum computing era.
- Global Collaboration on Research and Development (R&D):
- Governments, academia, and industries are collaborating on Research and Development to develop and implement quantum-safe solutions.
- Increased Awareness and Preparedness:
- Organizations, SMEs and governments are becoming more proactive in addressing quantum computing threats, driving investments in post-quantum cryptography (PQC) Research and Development.
- Quantum-Readiness Roadmaps:
- Organizations are creating roadmaps to transition to post-quantum cryptography (PQC), addressing challenges like “harvest now, decrypt later” threats.
- Future-Proofing Digital Infrastructure:
- Post-quantum cryptography (PQC) will play a critical role in ensuring the long-term security of digital systems as quantum computing capabilities evolve.
The journey to post-quantum cryptography (PQC) is a challenging but necessary transition to safeguard the future of digital operations, communications and transactions. These advancements highlight the urgency and innovation driving forward post-quantum cryptography (PQC).
Groundbreaking Impacts of Quantum Computing on Overall Cybersecurity
Quantum computing could revolutionize overall cybersecurity—both positively and negatively—by fundamentally altering how we protect data. Abbreviated hereafter is a breakdown of its potential impacts:
Negative Impacts:
- Breaking Current Encryption: As mentioned earlier, quantum computers could crack widely used public-key cryptographic systems like RSA and ECC, rendering much of today’s secure communications vulnerable.
- Data Harvesting Risks: Adversaries might collect encrypted data now with the intent to decrypt it in the future once quantum computers become advanced enough, compromising long-term data confidentiality.
- Undermining Digital Trust: If cryptographic systems fail, it could shake confidence in digital transactions, online banking, and other critical technologies.
- Cyber Arms Race: Nations and organizations may race to develop quantum capabilities, creating new threats and cyber espionage risks.
Positive Impacts:
- Quantum-Resistant Cryptography: The development of post-quantum cryptographic algorithms is underway to counteract quantum threats, creating new, stronger security measures.
- Enhanced Cyber Defense: Quantum-powered tools could identify and mitigate cyber threats faster by analyzing vast datasets more efficiently than classical computers.
- Quantum-Secure Key Distribution: Technologies like quantum key distribution (QKD) could enable virtually unbreakable encryption, leveraging the principles of quantum mechanics.
With reference to post-quantum cryptography (PQC), the very complex and multi-layered subject matter of our March 2025 Newsletter, the necessary transition to a quantum-safe future is vital to prevent harmful disruptions and maintain trust in digital systems. Post-quantum cryptography (PQC) is critically important because IT EPITOMIZES THE NEXT FRONTIER in protecting our digital infrastructure against future cyber threats and detrimental data breaches.
1 – Raj Badhwar (SVP & Chief Information Security Officer – CISO). The CISO’s Next Frontier: AI, Post-Quantum Cryptography and Advanced Security Paradigms. Softcover Edition published on the 8th of August 2022 by Springer Science + Business Media Publishing, 1 New York Plaza, New York City, USA, 430 pages. The CISO’s Next Frontier: AI, Post-Quantum Cryptography and Advanced Security Paradigms | SpringerLink
Resources and References
Christof Paar, Jan Pelzl and Tim Güneysu. Understanding Cryptography: From Established Symmetric and Asymmetric Ciphers to Post-Quantum Algorithms. Hardcover 2nd Edition published on the 16th of May 2024 by Springer-Verlag GmbH, Heidelberger Platz 3, 14197 City of Berlin, Germany, 543 pages. Understanding Cryptography: From Established Symmetric and Asymmetric Ciphers to Post-Quantum Algorithms | SpringerLink
Ravi Jay Gunnoo. Cybersecurity Education Compendium: Harnessing Digital Safety Best Practices Across the World. 1st Edition published in Paperback – Large Print Format and e-Book Version. Publication date: the 18th of September 2024. Publishing Company: Amazon Publishing USA, City of Seattle, State of Washington, USA, 728 pages. CYBERSECURITY EDUCATION COMPENDIUM: Harnessing Digital Safety Best Practices Across the World: Gunnoo, Ravi Jay: 9798336620344: Books – Amazon.ca
Douglas Robert Stinson and Maura B. Paterson. Cryptography: Theory and Practice – Textbooks in Mathematics. Paperback 4th Edition published on the 21st of January 2023 by Routledge/CRC Press – An Imprint of the Taylor & Francis Book LLC, 6000 Broken Sound Parkway NW, Boca Raton, Florida 33487-2742, United States of America, 598 pages. Cryptography: Theory and Practice – 4th Edition – Douglas Robert Stinson and Maura B. Paterson
Roger A. Grimes. Cryptography Apocalypse: Preparing for the Day When Quantum Computing Breaks Today’s Crypto. Paperback 1st Edition published on the 12th of November 2020 by John Wiley & Sons, Inc., 111 River Street, Hoboken, New Jersey 07030, United States of America, 272 pages. Cryptography Apocalypse: Preparing for the Day When Quantum Computing Breaks Today’s Crypto | Wiley
Stephen Paul Marsh. Formalising Trust as A Computational Concept: Doctoral Thesis on Computational Security. University of Sterling, Department of Computing Science and Mathematics, Scotland, 1994. Published in e-format by Google Books, 170 pages. Formalising Trust as a Computational Concept – Stephen Paul Marsh – Google Books
Ethan Westwood. Post-Quantum Cryptography: Beyond Quantum Threats: Unlocking the Unparalleled Security with PQC. Paperback Edition published on the 17th of December 2024 by Amazon USA Publishing, City of Seattle, State of Washington, United States of America, 203 pages. Post-Quantum Cryptography: Securing the Future of Digital Communications: Westwood, Ethan, Books, SMART: 9798304019866: Books – Amazon.ca
Government of Canada – Canadian Centre for Cyber Security. Cyber Security Guidance Awareness Series. Preparing your organization for the quantum threat to cryptography (ITSAP.00.017). February 2025. Preparing your organization for the quantum threat to cryptography (ITSAP.00.017) – Canadian Centre for Cyber Security
Government of the United States of America – NIST: Computer Security Resource Center (CSRC) – Information Technology Laboratory. Status Report on the 4th Round of the NIST Post-Quantum Cryptography Standardization. Post-Quantum Cryptography | CSRC
Sujoy Sinha Roy and Ingrid Verbauwhede. Lattice-Based Public-Key Cryptography in Hardware: Computer Architecture and Design Methodologies. Paperback 1st Edition published on the 25th of November 2020 by Springer-Verlag GmbH, Heidelberger Platz 3, 14197 City of Berlin, Germany, 201 pages. Lattice-Based Public-Key Cryptography in Hardware | SpringerLink
Jeffrey Hoffstein, Jill Pipher and Joseph H. Silverman. An Introduction to Mathematical Cryptography: Undergraduate Texts in Mathematics. Hardcover 2nd Edition published on the 11th of September 2014 by Springer Science + Business Media Publishing, 1 New York Plaza, New York City, United States of America, 538 pages. An Introduction to Mathematical Cryptography | SpringerLink
Government of the United States of America – National Institute of Standards and Technology – NIST: Computer Security Resource Center (CSRC) – Information Technology Laboratory. What is Post-Quantum Cryptography? What Is Post-Quantum Cryptography? | NIST
Government of Canada – CyberSecure Canada – Innovation, Science and Economic Development Canada. Certification Information and Certification Mark Display Requirements. CyberSecure Canada
Raj Badhwar (SVP & Chief Information Security Officer). The CISO’s Next Frontier: AI, Post-Quantum Cryptography and Advanced Security Paradigms. Softcover Edition published on the 8th of August 2022 by Springer Science + Business Media Publishing, 1 New York Plaza, New York City, USA, 430 pages. The CISO’s Next Frontier: AI, Post-Quantum Cryptography and Advanced Security Paradigms | SpringerLink
Contributions
Special thanks for the financial support of the National Research Council Canada (NRC) and its Industrial Research Assistance Program (IRAP) benefitting business organizations and SMEs throughout the 10 provinces and 3 territories of Canada.
Newsletter Executive Editor:
Alan Bernardi, SSCP, PMP, Lead Auditor for ISO 27001 and ISO 27701
B.Sc. Computer Science & Mathematics, McGill University, Canada
Graduate Diploma in Management, McGill University, Canada
Author-Amazon USA, Computer Scientist, Certified Professional Writer & Professional Translator:
Ravi Jay Gunnoo, C.P.W. ISO 24495-1:2023 & C.P.T. ISO 17100:2015
B.Sc. Computer Science & Cybersecurity, McGill University, Canada
B.Sc. & M.A. Professional Translation, University of Montreal, Canada


