By assigning an external party to review and assess your internal security controls through a recognized cybersecurity standard framework, you are demonstrating to your clients and your potential clients that your organization is serious about cybersecurity.
Some cybersecurity frameworks, such as PCI DSS for the Payment Card Industry Data Security Standard, are very exclusive to certain industries whereas others, namely SOC2 or ISO 27001, are more general and involves applicability across industries.
After duly acquiring compliance, each framework builds upon best practices to provide internal resources, clearly defined deliverables and operational processes in order to reduce risk and to provide a playbook (a set of rules and regulations) to respond to incidents calmly and purposefully (i.e., Incident Response Plan).
The documented functioning processes are accordingly adapted to the needs of the organization and they should be maintained and exercised on a regular basis to initiate cybersecurity behaviour within the company. Each cybersecurity control encompasses various requirements, associated costs for implementation, maintenance and audit. The cybersecurity controls should be carried out to scale depending on the size of the business.
Senior management needs to commit to the initial costs as well as the ongoing cost of preserving the compliance certification.
Introduction to Cybersecurity Frameworks
Contingent upon the reasons why your company is seeking a particular certification, there are several cybersecurity frameworks that can be put into operation. For example, it might be that your company wants to deal with internal security concerns, respond to a customer’s request for certification, or comply with an industry regulation. Many of the compliance frameworks have similar and overlapping control requirements to address cybersecurity risks. Before it starts the laborious task of obtaining certification, your company should choose the most appropriate control requirements to meet its needs. There are consulting companies to help you prepare for certification and walk you through the certification process. You will know you are ready when you are able
to confidently respond to the identified control requirements and ideally have line of sight, i‧e., unobstructed vision between the compliance framework requirement, process, and attestation.
The bottom line is that any security compliance framework is going to continuously improve a company’s cybersecurity posture. Each framework explains the need for security practices in a slightly different manner or focuses on aspects of security relevant to an industry.
This newsletter will not cover the CyberSecure Canada Compliance Framework because we have already dedicated our June 2022 Newsletter on that topic and it is available on In-Sec-M website.
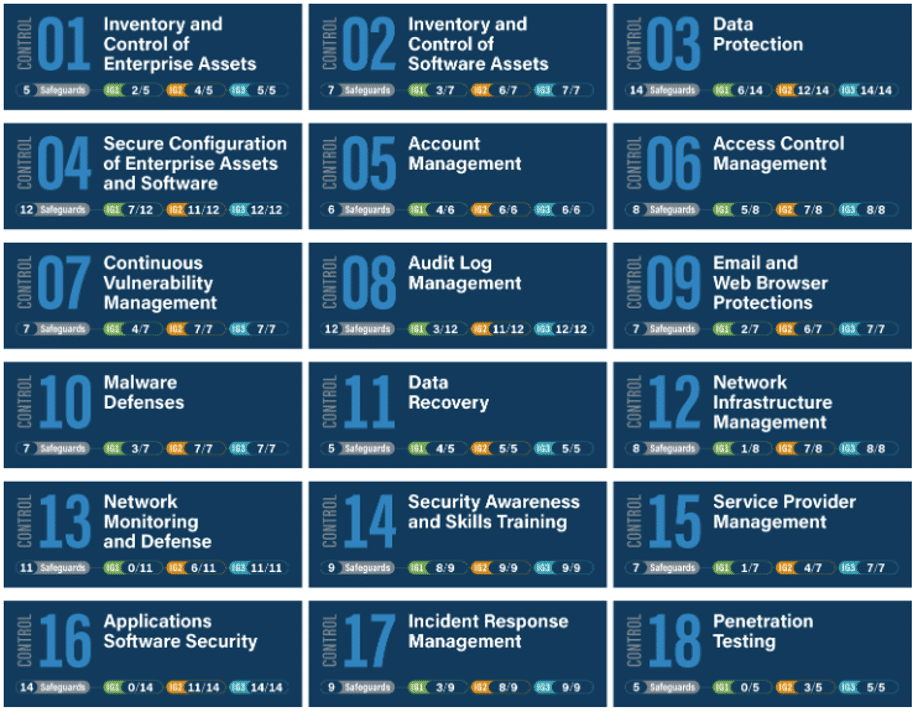
CIS

[1] https://www.cisecurity.org/controls
Primary Objective |
The CIS CSC is used to increase the security posture of businesses of all sizes. It takes a graduated approach to implementing security. |
How Long |
Small companies (5 to 20 employees) on average take approximately 20 to 25 hours to complete a CIS CSC assessment. The subsequent implementation can take anywhere from 1 to 6 months depending on the findings and the security implementation required. |
Costs |
Companies with under 20 employees see anywhere from $3,000 to $5,000 to assess and $10,000 to $40,000 to implement the foundational technology and processes. |
N.B.: CIS CSC should not be confused with the CyberSecure Canada Certification (CSC2) managed by the Government of Canada.
[2] https://ised-isde.canada.ca/site/cybersecure-canada/en
CMMC
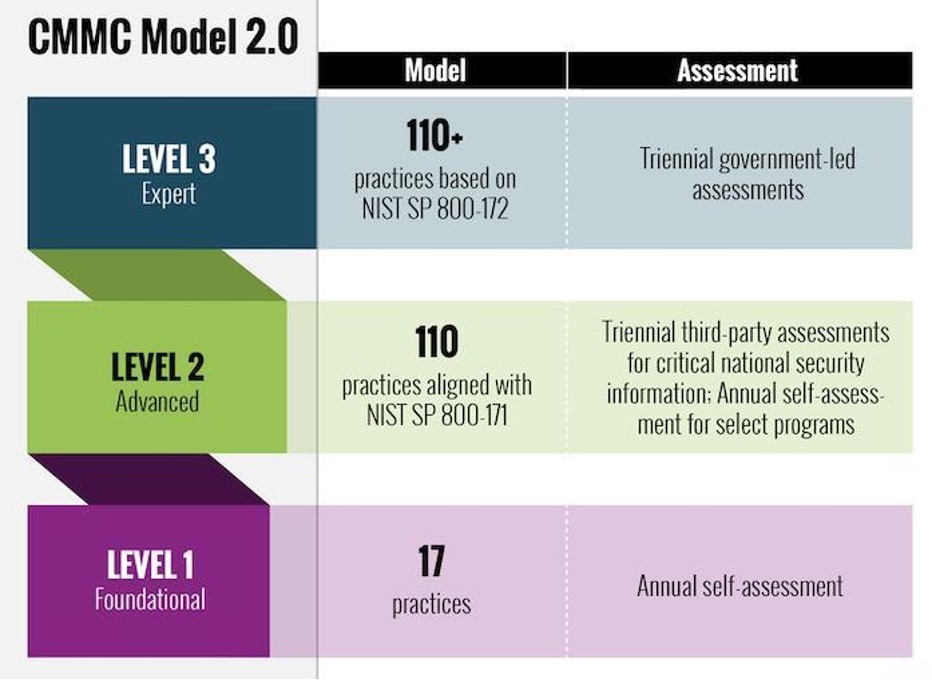
Cybersecurity Maturity Model Certification (CMMC3) was developed in 2002 to protect the United States industrial base against cyberattacks. CMMC 1.0 consisted of 17 cybersecurity domains and in 2021 revamped CMMC 2.0 to 14 cybersecurity domains. The CMMC certification draws upon the earlier work done by the National Institute of Standards and Technology (NIST). The certification realizes that organizations have different levels of security maturity within the framework. Version 2.0 controls are rated on a 3-level scale of process maturity and adherence to practices (Level 1 – Foundational to Level 3 – Expert). The assessment for a particular level is self-assess, third party, or government.
[3] https://www.acq.osd.mil/cmmc/
Primary Objective |
CMMC is a unified standard that considers the various information security standards and best practices that need to be implemented within the US defence industrial base supply chain to protect federal contract information and control unclassified information. |
How Long |
Depending on which of the three Levels of CMMC being pursued, it can take anywhere from 3 to 18 months. |
Costs |
The total annual assessment costs4 or each maturity level are as follows in US dollars:
[4] https://www.nationaldefensemagazine.org/articles/2021/6/8/the-pitfalls-of-factoring-in-security-and-cmmc-costs |
New cybersecurity requirements from the U.S. Department of Defense will have significant implications for Canadian manufacturers who hold existing contracts with the U.S. Department of Defense or plan to bid on contracts in the future.5 Currently, the Government of Canada does not have a similar certification requirement.
[5] https://www.bdo.ca/en-ca/insights/industries/manufacturing-distribution/key-changes-implications-cybersecurity-compliance/
ISO 27K

ISO/IEC 270016 is the International Organization for Standardization Certification related to best practices in Information Security Management Systems (ISMS) and there are more than a dozen standards within the family to address security of financial information, employee details, intellectual property and 3rd party intermediaries. It is a rigorous and comprehensive specification for protecting and preserving your data, files and confidential information under the principles of confidentiality, integrity, and availability.
[6] https://www.iso.org/isoiec-27001-information-security.html
Primary Objective |
ISO 27001 certification demonstrates that your organization has invested in the people, processes, and technology (e.g.: tools and systems) to protect your organization’s data and provides an independent, expert assessment of whether your data is sufficiently protected. Big companies such as Financial Institutions, Telecommunications, Technology, and Government Agencies (Healthcare) that have large amounts of sensitive data are good candidates for certification. Small and medium enterprises might be overwhelmed by the expenses and effort to obtain and maintain certification. |
How Long |
The ISO 27001 implementation process will depend on the size and complexity of the management system, but in most cases, small to mid-sized organizations can expect to complete the process within 6–12 months. |
Costs |
Small companies with under 50 employees typically see three to six audit days and overall costs from US $5,000 to US $10,000. The total cost per audit day varies by certification bodies, but a reasonable estimate is US $1,500 per day. Large enterprises can expect to pay US $100,000 + for initial ISO27001 compliance. |
ISO 28K
The recently updated ISO 280007 is an international standard which addresses the requirements of a Security Management System (SMS) for Supply Chains. Originally released in 2007, the compliance framework specifies to help the organization assess security threats and to manage them as they arise in many areas, including supply chains. Nowadays, threat actors are leveraging tightly coupled network connections from suppliers and customers to gain a foothold into organizations. ISO 28000 provides global best practices to supply chains management.
[7] https://www.iso.org/obp/ui/#iso:std:iso:28000:ed-2:v1:en
The standard is divided into 10 main clauses: |
|
Primary Objective |
The ultimate objective of ISO 28000 is to improve the security of supply chains. It is a high-level management standard that enables an organization to establish an overall supply chain security management system. ISO 28000 is typically adopted by larger organizations that deal with 100’s of suppliers. |
How Long |
ISO 28000 should take anywhere from 6 to 12 months, taking into account the size and maturity of the organization. |
Costs |
Similar to ISO 27000 certification |
SOC 2
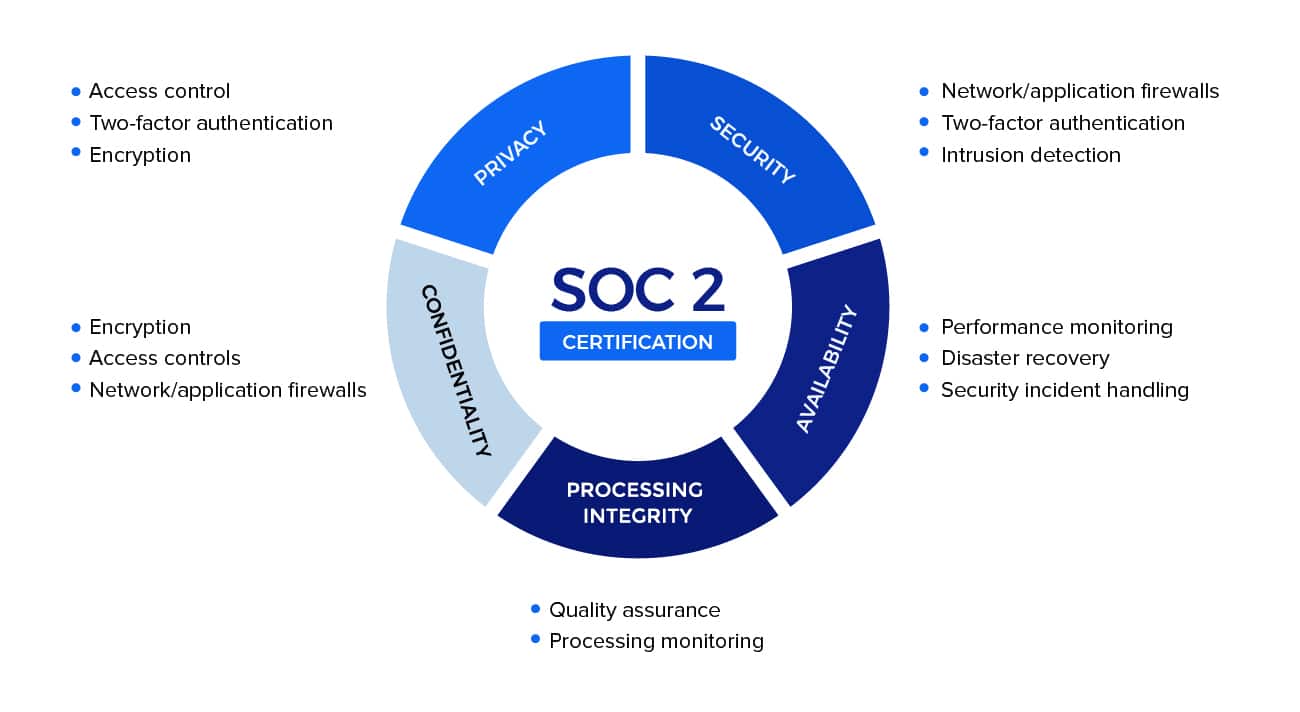
System and Organization Controls (SOC 2) Type I describe the systems related with an organization and they demonstrate whether the system design complies with the relevant trust principles, and Type II details the operational efficiency of these systems.
Developed by the American Institute of CPAs (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles”—security, availability, processing integrity, confidentiality, and privacy.
Within a service organization, these reports are intended to meet the needs of a broad range of users who need detailed information and assurance about the controls relevant to security, availability, confidentiality or privacy, and processing integrity of the systems that the service organization handles to process users’ data and the confidentiality and privacy of the information processed by these systems.
Primary Objective |
SOC 2 Type II examination demonstrates that an independent accounting and auditing firm has reviewed and examined an organization’s control objectives and activities and tested those controls to ensure that they are operating effectively. |
How Long |
Generating a SOC 2 Report will generally take somewhere between six months to a year for most companies. SOC 2 Type I Reports can take up to six months, whereas SOC 2 Type II Reports will typically take between six to twelve months. |
Costs |
The SOC 2 audit cost for Type II reports usually has a starting range anywhere from US $30,000 to US $100,000.
There are additional costs for:
|
Costs and Effort
Just like a new vehicle or house, there is the initial cost of the purchase, the cost of the factory upgrades, as well as annual maintenance expenses. Certification is not different from those expenses’ requirements. Costs and effort are commensurate to the size of the organization as well as the subdomains of the certification. As an example, SOC2 has five (5) Trust Services Criteria of Security, Availability, Processing Integrity, Confidentiality or Privacy that can separately be considered within scope – each with its own additional cost.
Control Infrastructure
What control infrastructure is currently in place? Is the inventory management system brand new, or will it need to be upgraded? Most organizations have systems in place as a regular course of business operations. Can these systems easily provide what is required by the certification audit or will there be a need for significant manual control to extract and verify the consistency of the relevant information. Also, ask yourself if the infrastructure covers the scope of the audit, such as mobile and remote devices.
Maintaining Control Requirements
Continuing with the analogy, if your organization has experience with certification (compliance), then costs should theoretically be less. One key to keeping costs consistent from year to year would be to have one dedicated person (or two) or an entire team whose responsibility it is to understand what internal and external resources are required, and maintain a compliance calendar of deliverables throughout the year. Then, there is the annual costs of the certification audit itself based on the maturity of the people, processes, and technology of the organization.
Audit
Security certification will consider a point in time review (ex. SOC2 Type I) that captures the controls in place and/or a period of time review (ex. SOC2 Type II) that captures controls and best practices being followed over time. As an example, many certifications have as a requirement for a penetration test against the IT infrastructure. Costs are proportional to the size of the infrastructure. The value of the audit is in the journey of thoroughly going through your company’s environment and understanding the processes and procedures required to meet them.
Some industries have specific compliance requirements such as the Payment Card Industry (PCI) that facilitate a common lexicon of controls for both merchants, intermediaries, and suppliers of credit cards. It is important that the organization understands why particular controls are in place and what potential risk is being mitigated. Security is an end-to-end ecosystem that is only as strong as its weakest link.
Other Frameworks and Regulations
North American Electric Reliability Corporation – Critical Infrastructure Protection (NERC-CIP)8 standards are the mandatory security standards that apply to entities that own or manage facilities that are part of the U.S. and Canadian electric power grid.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA)9 is a US federal law that requires the creation of national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge. HIPAA “certification” is a third-party process meant to aid your organization’s HIPAA compliance.
The General Data Protection Regulation (GDPR)10 is the toughest privacy and security law in the world. Though it was drafted and passed by the European Union (EU), it imposes obligations onto organizations anywhere, so long as they target or collect data related to people in the EU.
The Office of the Superintendent of Financial Institutions (OSFI)11 is an independent agency of the Government of Canada, established in 1987 to contribute to the safety and soundness of the Canadian financial system.
OSFI supervises and regulates federally registered banks and insurers, trust, and loan companies, as well as private pension plans subject to federal oversight.
The Payment Card Industry Data Security Standard (PCI DSS)12 is a set of security standards formed in 2004 by Visa, MasterCard, Discover Financial Services, JCB International and American Express. Governed by the Payment Card Industry Security Standards Council (PCI SSC), the compliance scheme aims to secure credit and debit card transactions against data theft and fraud.
[8] https://www.nerc.com/pa/Stand/Pages/USRelStand.aspx
[9] https://www.cdc.gov/phlp/publications/topic/hipaa.html
[10] https://gdpr.eu/
[11] https://www.osfi-bsif.gc.ca/Eng/osfi-bsif/Pages/default.aspx
[12] https://www.pcisecuritystandards.org
Summary
There are a variety of cybersecurity compliance frameworks to choose from as a function of the organization’s industry, size, regulatory environment, and budget. Initial costs, as well as ongoing costs need to be understood. Cybersecurity frameworks are continuously being updated with current best practices to mitigate the evolving threat landscape. As a result, make sure you are using the most recent version.
Start your compliance journey with the straightforward CIS CSC framework or the requirements from CMMC that are applicable. While doing so, you will get an overall idea of what most frameworks are about. Graduate to the more complex SOC 2 or ISO compliance frameworks as required. Only choose to go down the PCI DSS route if you deal with credit card transactions. Whatever business orientation will your company undertake, the cybersecurity compliance framework journey will benefit it in the long run.


